The Most Useful Sites for Browser Testing

Here is a list of the most useful and trusted websites for browser security testing.
Am I Unique?
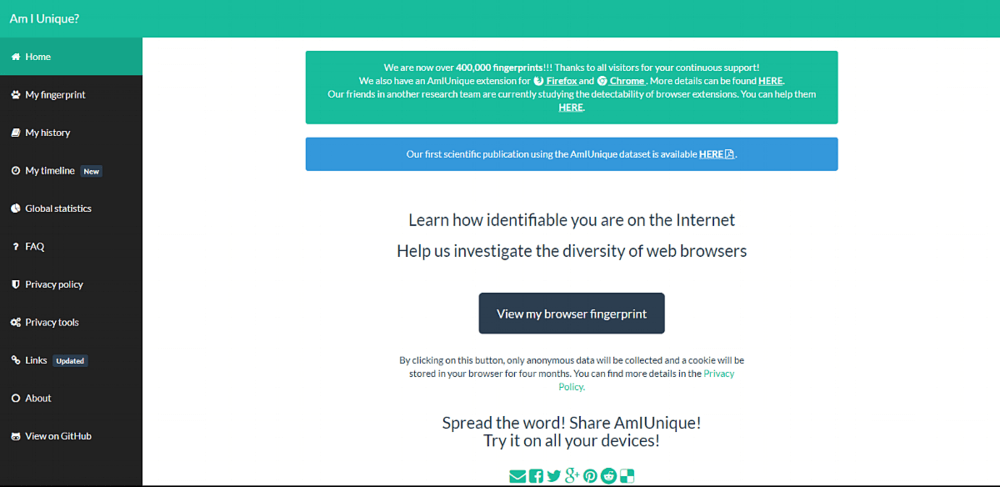
Am I Unique is a browser fingerprint analyzer that has two goals in mind;
Inform users about their position within the web ecosystem
With this web site, we aim at providing users with some basic information about their configuration and how trackable it is. We also want to exploit the data we collect to advise users about how they can be more similar to others and thus be less trackable.
Investigate the diversity of fingerprints
The research question we investigate is: how can we automatically reconfigure a users platform to fuzz the device fingerprint in a realistic manner? The degree of realism is important to prevent users of our solution to be detected as such. The collection of a large base of real fingerprints will allow us to tune our solution towards platforms that are as different as possible yet not distinguishable as “strange” configurations.
Browser Leaks
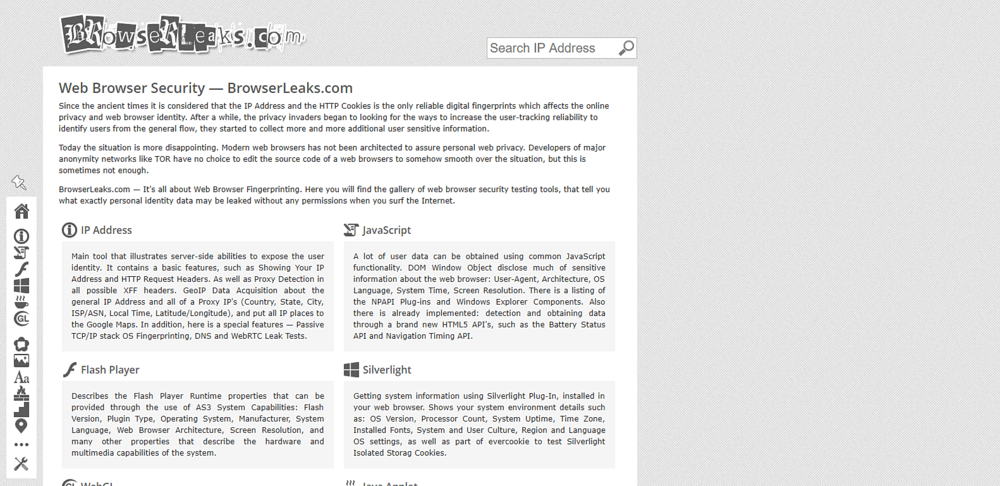
Since the ancient times it is considered that the IP Address and the HTTP Cookies is the only reliable digital fingerprints which affects the online privacy and web browser identity. After a while, the privacy invaders began to looking for the ways to increase the user-tracking reliability to identify users from the general flow, they started to collect more and more additional user sensitive information.
Today the situation is more disappointing. Modern web browsers has not been architected to assure personal web privacy. Developers of major anonymity networks like TOR have no choice to edit the source code of a web browsers to somehow smooth over the situation, but this is sometimes not enough.
Hence, comes the creation of BrowserLeaks. It’s all about Web Browser Fingerprinting. Here you will find the gallery of web browser security testing tools, that tell you what exactly personal identity data may be leaked without any permissions when you surf the Internet.
DNS Leak Test
What is a DNS leak and why should I care?
When using an anonymity or privacy service, it is extremely important that all traffic originating from your computer is routed through the anonymity network. If any traffic leaks outside of the secure connection to the network, any adversary monitoring your traffic will be able to log your activity.
DNS or the domain name system is used to translate domain names such as www.privacyinternational.org into numerical IP addresses e.g. 123.123.123.123 which are required to route packets of data on the Internet. Whenever your computer needs to contact a server on the Internet, such as when you enter a URL into your browser, your computer contacts a DNS server and requests the IP address. Most Internet service providers assign their customers a DNS server which they control and use for logging and recording your Internet activities.
Under certain conditions, even when connected to the anonymity network, the operating system will continue to use its default DNS servers instead of the anonymous DNS servers assigned to your computer by the anonymity network. DNS leaks are a major privacy threat since the anonymity network may be providing a false sense of security while private data is leaking.
If you are concerned about DNS leaks, you should also understand transparent DNS proxy technology to ensure that the solution you choose will stop
IP Leak
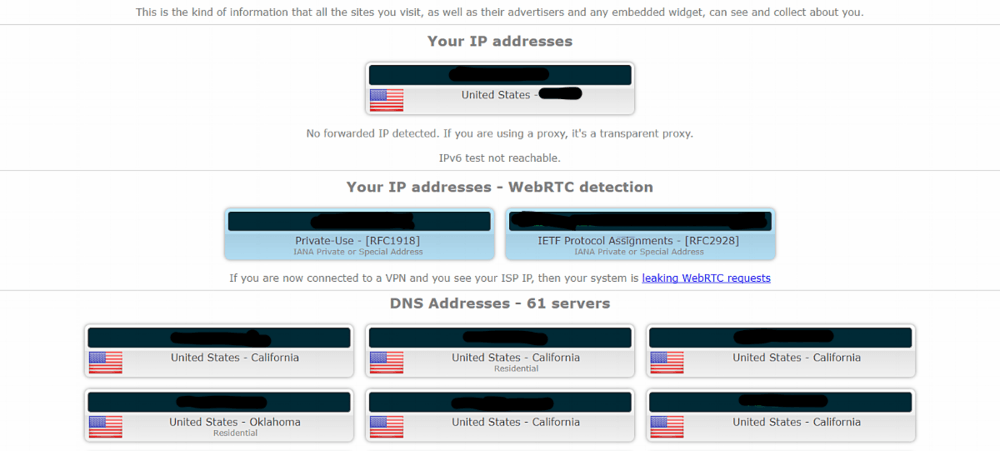
What is a “WebRTC leaks”?
WebRTC implement STUN (Session Traversal Utilities for Nat), a protocol that allows to discover the public IP address. To disable it:
Mozilla Firefox: Type “about:config” in the address bar. Scroll down to “media.peerconnection.enabled”, double click to set it to false.
Google Chrome: Install Google official extension WebRTC Network Limiter.
Opera: Type “about:config” in the address bar or go to “Settings”. Select “Show advanced settings” and click on “Privacy & security”. At “WebRTC” mark select “Disable non-proxied UDP”.
What is a “DNS leaks”?
In this context, with “DNS leak” we mean an unencrypted DNS query sent by your system OUTSIDE the established VPN tunnel.
Why my system suffers DNS leaks?
In brief: Windows lacks the concept of global DNS. Each network interface can have its own DNS. Under various circumstances, the system process svchost.exe will send out DNS queries without respecting the routing table and the default gateway of the VPN tunnel, causing the leak.
Should I be worried for a DNS leak?
If you don’t want that your ISP, and anybody with the ability to monitor your line, knows the names your system tries to resolve (so the web sites you visit etc.) you must prevent your system to leak DNS. If you feel that you’re living in a human rights hostile country, or in any way the above mentioned knowledge may harm you, you should act immediately to stop DNS leaks.
How Does Torrent Detection Work?
To detect data from your torrent client we provide a magnet link to a fake file. The magnet contains an http url of a controlled by us tracker which archives the information coming from the torrent client.
What Is My IP Address?

Your IP address is something you probably rarely think about, but it’s vitally important to your online lifestyle. Without an IP address, you wouldn’t be able to get today’s weather, check the latest news or look at videos online.
Why?
Because without your IP address, websites like whatismyipaddress.com, CNN or ESPN wouldn’t know where to send the information you asked for. They wouldn’t be able to get it to YOUR computer.
Mr. Whoer
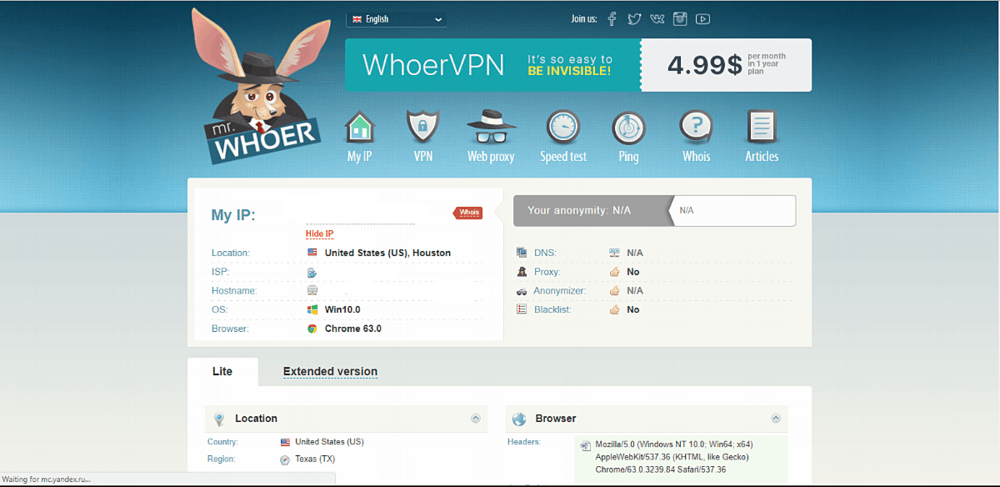
Whoer.net is a service aimed at verifying the information your computer sends to the web.
It is perfect for checking proxy or socks servers, providing information about your VPN server and scanning black lists for your IP address. The service shows whether your computer enables Flash and Java, as well as its language and system settings, OS and web-browser, define the DNS etc.
The main and the most powerful side of our service is the interactive checking by Java, Flash and WebRTC, allowing to detect the actual system settings and its weaknesses, which can be used by third-party resources to find out the information about your computer.
