Here Is a List of NSA Partners

Domestic Surveillance is a team sport. The NSA’s success depends upon their partnership with other federal, state, and local agencies. The USA PATRIOT Act was passed in 2001 for the purpose of “Uniting and Strengthening America by Providing Appropriate Tools Required to Intercept and Obstruct Terrorism”. This far-reaching law gave them a wide range of new tools to detect and prevent terrorism. Their partners transmit a steady flow of intelligence information 24-hours a day from across the nation. The incoming data is indexed, stored, and shared throughout the Intelligence Community on their massive cloud computing network.
The Hacking Team

Hotplug Field Kit
The Equation Group

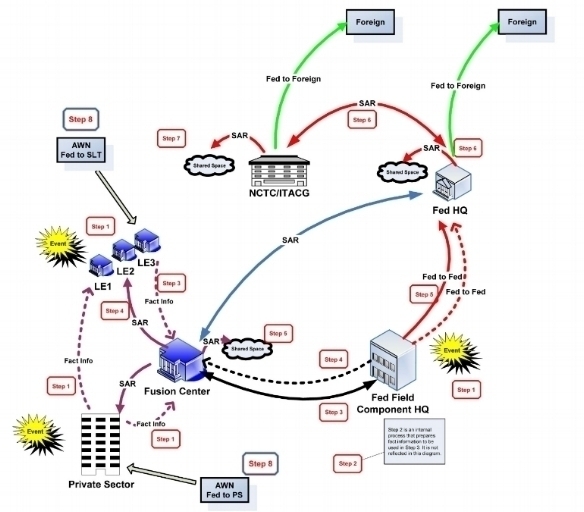
Suspicious Activity Reporting – Fusion Centers
The Nationwide Suspicious Activity Reporting (SAR) Initiative (NSI) is a collaborative effort led by the U.S. Department of Justice in partnership with the Department of Homeland Security, the FBI, and state and local law enforcement partners. This initiative establishes a national capacity for gathering, documenting, processing, analyzing, and sharing SAR information gathered by fusion centers across the county.
Located in states and major urban areas, fusion centers are uniquely situated to empower front-line law enforcement, public safety, fire service, emergency response, public health, and private sector security personnel to gather and share domestic threat-related information.
Suspicious Activity Reporting (SAR) Information Flow
National Counter-terrorism Center
The National Counterterrorism Center (NCTC) operates as a partnership of more than 16 organizations including the CIA, FBI, State Department, Defense Department, Homeland Security; and other agencies that provide unique expertise such as the Departments of Energy, Treasury, Agriculture, Transportation, and Health and Human Services.
The NCTC is the primary organization for analyzing and integrating all foreign and domestic terrorism-related intelligence possessed or acquired by the United States. It was also recently given the authority to examine the government files of U.S. citizens for possible criminal behavior, even if there is no reason to suspect them.
FBI Terrorist Screening Center

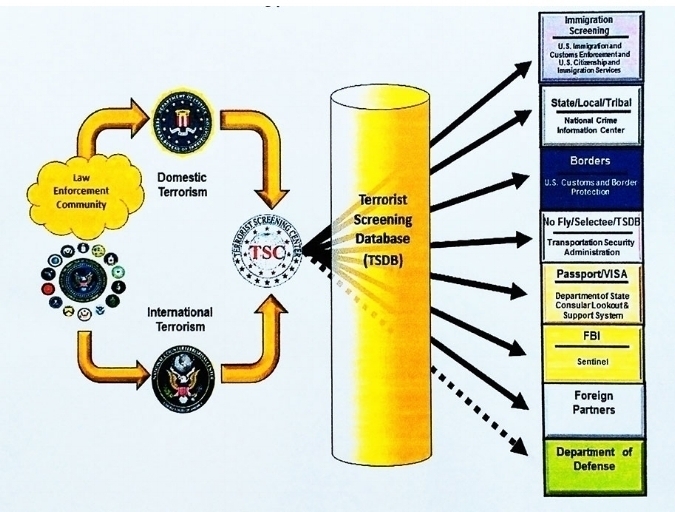
The FBI Terrorist Screening Center (TSC) was established in 2003 by Homeland Security Presidential Directive 6 which directed that a center be established to consolidate the government’s approach to terrorism screening. The TSC maintains the U.S. government’s consolidated Terrorist Watch list, a single database of identifying information about those known or reasonably suspected of being involved in terrorist activity.
FBI airplanes equipped with high-tech cameras and sophisticated surveillance technology capable of tracking thousands of cellphones below fly circular routes daily around many major U.S. cities tracking targets and gathering intelligence. The clickable map below shows the unusual flight patterns in some of the targeted areas.
FBI
The FBI is the NSA’s go-to partner for much of their nation’s domestic surveillance needs:
- Information collected from the use of National Security Letters authorized by the PATRIOT Act
- Phone calls and text messages from the FBI Digital Collection System (DCSNet)
- “Google-like” search capability of citizen information from the FBI Law Enforcement National Data Exchange Program (N-DEx)
- Cell phone location tracking from the Stingray “IMSI catchers” (International Mobile Subscriber Identity) masquerading as cell phone towers
- Massive FBI data-mining project with more than 1.5 billion government and private-sector records about citizens and foreigners collected by the FBI’s National Security Analysis Center(NSAC)
CIA
The Central Intelligence Agency has publicly committed to increasing its data collection efforts. CIA Chief Technology Officer Gus Hunt explains why: “The value of any piece of information is only known when you can connect it with something else that arrives at a future point in time. Since you can’t connect dots you don’t have, we fundamentally try to collect everything and hang on to it forever.”
DHS
TSA airline passenger data; surveillance data from unmanned domestic Predator B drones patrolling the northern and southern borders
Treasury
Cash Transaction Reporting and Suspicious Activity Reporting data
U.S. Postal Service
The exterior of every piece of paper mail processed in the United States is photographed and stored by the “Mail Isolation Control and Tracking program”. Some post offices have installed hidden cameras outside to capture and record the license plates and facial features of customers leaving the parking lots.
United States Congress
In 2011, Congress extended three key provisions of the PATRIOT Act for another four years. In 2012, Congress reauthorized the FISA Amendments Act. In 2015, both houses of Congress passed the USA Freedom Act which legally codifies our dragnet data collection while happily appeasing the civil liberties folks (a double win!).
State/Local Government
Electronic transit cards; electronic toll collectors; vehicle information and location data captured by license plate readers; public transportation video/audio surveillance systems
British Spy Aagency GCHQ
The GCHQ (UK Government Communications Headquarters) through its “Mastering the Internet” and “Global Telecoms Exploitation” programs uses secret agreements with commercial companies allowing them to tap into the transatlantic fiber-optic cables carrying the world’s phone calls and internet traffic. The GCHQ processes, stores, and shares this information with the NSA via the Tempora program.
Yahoo!
Secretly searches all of its customers’ incoming emails for specific character strings provided by the NSA/FBI.
Latest Posts
- CEO/Executive Contact List
- Almost Everyone Involved In Developing Tor Was (Is) Funded by the US Government
- How to Use Social Media Apps Without Google or Apple’s Permission
- How to Hack an FTP Login
- How to Hack Home Routers
- How to Track Someone By Phone
- How to RAT Someone’s Computer
- How to Launch a DoS/DDoS Attack
- WordPress vs Joomla vs Drupal
- How to Hack Security Cameras with Google
