Best Hacking Tools of 2026
Crypters
Aegis 🆓/💲
Aegis Crypter is one the most popular FUD crypers in the world. FUD crypters can be used to encrypt viruses, RATs, keyloggers, spyware, etc. to make them undetectable from antiviruses. When these .exe files are encrypted with FUD crypters they become undetectable to antiviruses as well.
Insanity Protector 🆓
Insanity Protector is a powerful FUD Crypter.
Debuggers
GDB 🆓
GDB is a GNU Project debugger. The unique feature of this debugger enables the user to see what is happening inside one program while it is being executed or check a program at the moment of the crash.
Immunity Debugger 🆓
Immunity Debuggr is a powerful debugger for analyzing malware. Its unique features include an advanced user interface with heap analysis tool and function graphing.
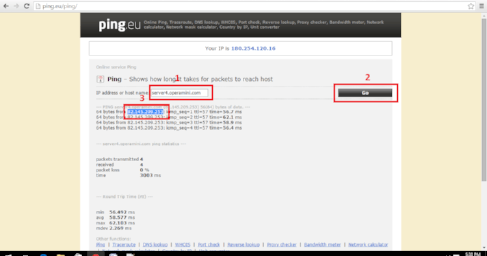
Ping.eu 🆓
Ping.eu is a tracing tool that helps the user to know the time that the data packets took to reach the host. This is an online application where you just need to place the host name or IP address and fetch the result.
Encryption Tools
Truecrypt 🆓
TrueCrypt is open source encryption tool which can encrypt a partition in the Windows environment (except Windows 8); it’s equipped for creating a virtual encrypted disk in a file. Moreover, it has the capability to encrypt the complete storage device. TrueCrypt can run on different operating systems like Linux, Microsoft Windows, and OSX. TrueCrypt stores the encryption keys in the RAM of the computer.
OpenSSH 🆓
OpenSSH is the short name for Open Secure Shell and is a free software suite which is used to make your network connections secured. It uses the SSH protocol to provide encrypted communication sessions in a computer network. It was designed originally as an alternative to the Secure Shell Software developed by SSH Communications Security. The tool was designed as a part of the OpenBSD project.
OpenSSL 🆓
OpenSSL is an open source encryption tool which implements the TLS and SSL protocols. OpenSSL’s core library is written in the C programming language. The fundamental cryptographic functions are implemented by it. OpenSSL versions are available for operating systems like UNIX, Solaris, Linux and Mac OS X. The project was undertaken in 1988 with the objective of inventing free encryption tools for the programs being used on the internet.
Tor 🆓
Tor is a free encryption tool and has the capability to provide online anonymity as well as censorship resistance. Internal traffic is directed through a free network which consists of more than five thousand relays so that the user’s actual location can be hidden. It is difficult to track the Internet activities like visiting websites and instant messages; the most important goal of this tool is to ensure the personal privacy of the users.
OpenVPN 🆓
OpenVPN provides a full-featured open source SSL VPN solution that accommodates a wide range of configurations, including remote access, site-to-site VPNs, Wi-Fi security, and enterprise-scale remote access solutions with load balancing, failover, and fine-grained access-controls.
Exploitation
Metasploit 🆓
Metasploit was released in the year 2004 and it was an instant hit in the world of computer security. Metasploit provides data on the vulnerabilities in the security system and it helps in conducting penetration testing too.
Router Scan 🆓
Router Scan is able to find and identify a variety of devices from large number of known routers and that the most important thing is to get from them useful information, in particular the characteristics of the wireless network: a method of protecting the access point (encryption), access point name (SSID) and access point key (passphrase). It also has the ability to show information about the WAN connection (useful when scanning a local network) and show the model of router.
BeEF 🆓
BeEF is the short term for The Browser Exploitation Framework. It is a tool for penetration testing which concentrates on a web browser and thus accesses the actual security position of the environment it’s targeting.
KMSpico Windows 10 Activator 🆓
KMSpico is the most popular tool for activating Windows 10 without a product key.
Windows 8 Activator 🆓
Windows 8 Activator is the most popular tool for activating Windows 8 without a product key.
Windows 7 Loader 🆓
Windows 7 Loader is the most popular tool for activating Windows 7 without a product key.
Windows XP Activator 🆓
Windows XP Activator is the most popular tool for activating Windows XP without a product key.
Forensics
Sleuth Kit 🆓
Sleuth Kit is an open source digital intervention or forensic toolkit. It runs on varied operating systems including Windows, Linux, OS X and many other Unix systems. It can be used for analyzing disk images along with in-depth analysis of file systems like FAT, Ext3, HFS+, UFS and NTFS.
Helix 🆓
Helix is a Linux based incident response system. It is also used in system investigation and analysis along with data recovery and security auditing. The most recent version of this tool is based on Ubuntu that promises ease of use and stability.
Government Malware
FinFisher (NSA) 🆓
FinFisher, also known as FinSpy, is surveillance software marketed by Lench IT Solutions plc, which markets the spyware through law enforcement channels. FinFisher can be covertly installed on targets’ computers by exploiting security lapses in the update procedures of non-suspect software. The company has been criticized by human rights organizations for selling these capabilities to repressive or non-democratic states known for monitoring and imprisoning political dissidents. Egyptian dissidents who ransacked the offices of Egypt’s secret police following the overthrow of Egyptian President Hosni Mubarak reported that they had discovered a contract with Gamma International for €287,000 for a license to run the FinFisher software. In 2014, an American citizen sued the Ethiopian government for surreptitiously installing FinSpy onto his computer in America and using it to wiretap his private Skype calls and monitor his entire family’s every use of the computer for a period of months.
DoublePulsar (NSA) 🆓
DoublePulsar is a backdoor implant tool developed by the U.S. National Security Agency’s Equation Group that was leaked by The Shadow Brokers in early 2017.
Stuxnet (NSA) 🆓
Stuxnet is a malicious computer worm, first uncovered in 2010 by Kaspersky Lab. Thought to have been in development since at least 2005, Stuxnet targets SCADA systems and was responsible for causing substantial damage to Iran’s nuclear program. Although neither country has openly admitted responsibility, the worm is believed to be a jointly built American/Israeli cyberweapon.
Equation Group (❓) 🆓
The Equation Group, classified as an advanced persistent threat, is the code name for the Tailored Access Operations (TAO) unit of the United States National Security Agency (NSA). Kaspersky Labs describes them as one of the most sophisticated cyber attack groups in the world and “the most advanced … we have seen”, operating alongside but always from a position of superiority with the creators of Stuxnet and Flame. Most of their targets have been in Iran, Russia, Pakistan, Afghanistan, India, Syria, and Mali.
Keyloggers
Revealer Keylogger 🆓
Revealer Keylogger is a invisible and free keylogger for Windows 10, 8, 7, Vista or XP. It allows you to monitor user activity on your computer.
Network Hacking Tools
Nmap 🆓
Nmap or Network Mapper is a free open source utility tool for network discovery and security auditing solution for you. It is a flexible, powerful, portable and easy-to-use tool that is supported by most of the operating systems like Linux, Windows, Solaris, Mac OS and others.
SuperScan 🆓
SuperScan is a multi-functional application that is designed for scanning TPC ports. This is also a pinger and address resolver. It also has useful features like ping, traceroute, WhoIs and HTTP request. There is no need of installation as it is a portable application.
Angry IP Scanner 🆓
Angry IP Scanner is a fast port and IP address scanner. It is a lightweight and cross-platform application that has the capacity to scan the IP addresses in any range and also in their ports. It simply pings each IP address.
Packet Crafting
Hping 🆓
Earlier Hping was used as a security tool. Now it is used as a command-line oriented TCP/IP packet analyzer or assembler. You can use this for Firewall testing, advanced port scanning, network testing by using fragmentation, TOS, and different other protocols.
Scapy 🆓
Scapy is a powerful and interactive packet manipulation program. Scapy has the capability to decode or forge the packets of a large number of protocols at a time. One of the best features is that it can confuse the process of decoding and interpreting.
Ostinato 🆓
Ostinato is a network traffic generator and network test tool. You can load test and functional test with many protocols. It comes with a GUI and Python API. It is supported on Windows, Linux, Mac OSX, and BSD.
Packet Sniffers
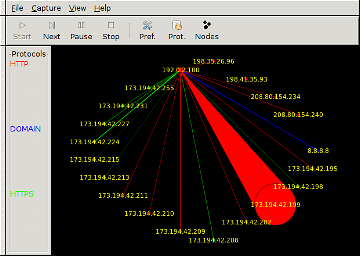
Wireshark 🆓
If you want to input a security system, Wireshark is the must-have security tool. It monitors every single byte of the data that is transferred via the network system. If you are a network administrator or penetration tester this tool is a must have.
TCPDUMP 🆓
TCPDUMP is a command-line packet analyzer. After completing the designated task of packet capturing TCPDUMP will throw the report that will contain numbers of captured packet and packets received by the filter. The user can use flags like –v, -r and –w to run this packet analyzer tool.
EtherApe 🆓
EtherApe is graphical network monitor for UNIX model PCs after etherman. This interactive tool graphically displays network activity. It features link layer and TCP/IP modes. It supports Token Ring, FDDI, Ethernet, PPP, SLIP, ISDN and other WLAN devices. Web Proxies: Proxies fundamentally assist in adding encapsulation to distributed systems. The client can request an item on your server by contacting a proxy server.
Password Crackers
Kon-Boot 🆓/💲
Kon-Boot is an application which will silently bypass the authentication process of Windows based operating systems. Without overwriting your old password! In other words you can login to your Windows profile without knowing your password. Easy to use and excellent for tech repairs, data recovery and security audits.
Brutus 🆓
Brutus is one of the most flexible and free password crackers which operates remotely. It is popular also because of its high speed and operates under operating systems such as Windows 2000, Windows NT and Windows 9x. Currently, it does not operate under the UNIX operating system. Brutus was initially designed to check network devices like routers for common as well as default passwords.
Ophcrack 🆓
Ophcrack is a free password cracker software which is based on the effective implementation of the rainbow tables. It runs on a number of Operating Systems like Mac OS X, Unix/Linux and Windows Operating System. It is equipped with real-time graphs for analyzing the passwords and is an open source software. Ophcrack has the capability to crack both NTLM hashes as well as LM hashes.
John the Ripper 🆓
John the Ripper is a free software for password cracking which was originally designed for the Unix Operating System. At present, it can run on 15 Operating systems which include 11 different versions of UNIX, Win32, DOS, and BeOS. It has the capability to combine several password crackers into a single package which has made it one of the most popular cracking tools for hackers.
RATs (Remote Access Tool)
DarkComet 🆓
DarkComet is the most popular remote administration tool in the world. While no longer maintained, it is still incredibly featured, powerful, and very stable.
njRAT 🆓
njRAT is a great remote administration tool with good features and very stable.
QuasarRAT 🆓
Quasar is a fast and light-weight remote administration tool coded in C#. Providing high stability and an easy-to-use user interface, Quasar is a fantastic remote administration solution.
Rootkit Detectors
HijackThis 🆓
HijackThis is a free and open-source tool to detect malware and adware on Microsoft Windows. It was originally created by Merijn Bellekom, and later sold to Trend Micro. The program is notable for quickly scanning a user’s computer to display the most common locations of malware, rather than relying on a database of known spyware.
AIDE 🆓
AIDE (Advanced Intrusion Detection Environment) is a directory and file integrity checker that helps in creating a database using the regular expression rules that it finds from the config files. This tool also supports message digest algorithms and file attributes like File type, Permissions, Inode, Uid, Gid, and others.
Netfilter 🆓
Netfilter offers software for the packet filtering framework that works within the Linux 2.4.x and later series of the kernel. The software of Netfilter help in packet mangling including packet filtering along with network address and port translation.
Traffic Monitoring Tools
Splunk 🆓
If you want to convert your data into powerful insights Splunk tools are the best options for you. The Splunk tools are the leading platforms for operational intelligence. It can collect any type of data from any machine in real time.
Nagios 🆓
Nagios is the name for the industry standard in monitoring IT infrastructure. The Nagios tools help you monitor your entire IT infrastructure and have the capability to detect problems well ahead they occur. It can also detect security breaches and share data availability with stakeholders.
Ngrep 🆓
Ngrep or network grep is a pcap-aware tool that allows you to extend hexadecimal or regular expressions in order to match it against the data loads of the packet. It can recognize IPv4/6, UDP, TCP, Ethernet, SLIP, PPP, FDDI and many others.
Vulnerability Scanners
Nessus 🆓
Nessus is the world’s most popular vulnerable scanner topping the list in the years 2000, 2003 and in the year 2006 survey on security tools. It’s free to use vulnerability scanner for personal use in the nonenterprise environment.
OpenVAS 🆓
OpenVAS scanner is tipped by many to be the most advanced vulnerability scanner in the world and is a powerful and comprehensive tool for scanning as well as providing solutions for vulnerability management. It is free software and is maintained daily.
Nipper 🆓
Nipper is a parser for network infrastructure and its full form is Network Infrastructure Parser. This open source scanner helps with features like auditing, configuring and managing devices for network infrastructure as well as managing the computer networks.
Web Vulnerability Scanners
Burp Suite 🆓/💲
Burp Suite is a tool for conducting the security test of web-based applications. It has a collection of tools which work together and conduct the entire process of testing with an objective to find as well as exploit the vulnerabilities in the security.
Webscarab 🆓
Webscarab is a testing tool for web security applications and has been written in Java and thus is operating system independent. It acts as a proxy and lets users change web requests by web browsers and web server replies. Webscarab often records the traffic to conduct a further review.
Websecurify 🆓
Website security is a crucial factor for both personal as well as organization websites. The prime goal should be to detect the vulnerability of your website before an intruder detects it. Websecurify is a testing tool for website security and can be used to detect the vulnerability of your webs
Wireless Hacking Tools
Aircrack-ng 🆓
Aircrack-ng is a software suite specially designed for a wireless network and which operates under both the Windows and the Linux Operating System. Aircrack-ng consists of a packet sniffer, WPA cracker, and analysis tool and a detector for the wireless Local Area Networks (802.11). The best part of this software suit is one need not install it to use it. It is a collection of files which can be easily used with a command prompt.
Airsnort 🆓
AirSnort is a wireless LAN (WLAN) tool which cracks encryption keys on 802.11b WEP networks. AirSnort operates by passively monitoring transmissions, computing the encryption key when enough packets have been gathered.
Kismet 🆓
Kismet is a wireless detector system which detects possible intrusion to an 802.11 layer2 wireless network, it is also a sniffer. There is certain plug-in supported by Kismet which enables sniffing media like DECT. It also has the capacity to infer whether a nonbeaconing network is present or not via the data traffic in the network and a network is identified by this tool by collecting data packets passively, detecting hidden and standard named networks.
Latest Posts
- CEO/Executive Contact List
- Almost Everyone Involved In Developing Tor Was (Is) Funded by the US Government
- How to Use Social Media Apps Without Google or Apple’s Permission
- How to Hack an FTP Login
- How to Hack Home Routers
- How to Track Someone By Phone
- How to RAT Someone’s Computer
- How to Launch a DoS/DDoS Attack
- WordPress vs Joomla vs Drupal
- How to Hack Security Cameras with Google